
Yesterday, I found two of my cloud servers had been hacked. The servers’ CPU was always 100% and I found a suspicious process. After terminating the suspicious process, the system got back normal and CPU was no longer 100%. However, the suspicious process came back and CPU was 100% again. So I cleaned the whole system by checking my ssh public-key authentication file, cron job, deleting all malicious files and stopping all unnecessary services. I was watching the system whole day and the virus didn’t come back.
Now I am sure that the system is clean and I have to start all services on the system. But this could open the gates for hackers again. Right now, I still don’t know how hackers break my system and send the virus in system. It could be highly possibly because of following services which are running on the system:
- Shadowsocks Server
- Redis
Both of them are opening the port to provide the service from a specific IP address. Therefore, we can simply set some access rules to allow the specific IP to access and deny the others. Linux system provides a very powerful tool Netfilter to limit the incoming network access. We can use the IPTables to set the rules and apply the in Netfilter. This way can efficiently protect the server from hacking and keep our Linux server away from malware.
Check IPTables Status
Before we start to setup access rules, we can check the IPTables status with following command:
service iptables status
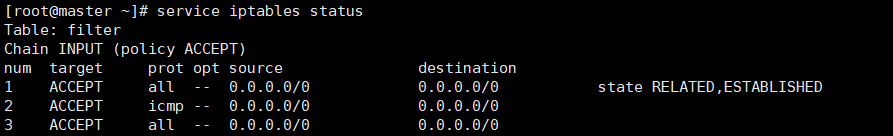
Sometimes, you could get this error message:
Redirecting to /bin/systemctl status iptables.service
Unit iptables.service could not be found.
So you need to install the iptables-services with following command:
yum install iptables-services
For more information, you can check this post: https://stackoverflow.com/questions/24756240/how-can-i-use-iptables-on-centos-7
Setup IPtables Rules
We can setup the access rules by editing the IPTables configuration file. The config file is located here:
/etc/sysconfig/iptables
My config file looks like:

According to above rules, it opens the gate for every connections. If we only want our server to accept the connections from a specific IP. For example, we want to provide the ShadowSocks service on port 8388.
We can put following line in the config:
-A INPUT -p tcp -s 10.89.64.6 --dport 3306 -j ACCEPT #10.89.64.6 is your source IP

After start the iptable service, only the computer with “10.89.64.6” IP address can access the 8388 port. Currently, we enables the IPtables to protect our server from unsafe access.